사업설명 Exploring How VPNs Empower Users to Take Control and Opt-Out of Data B…
페이지 정보

본문

In today's interconnected world, safeguarding personal information has become increasingly important. Many individuals are unaware of how their online presence is constantly monitored. Every click and interaction can be tracked, leading to unwanted exposure. This growing concern around privacy has sparked interest in protective technologies that can help maintain anonymity.
Strategies to enhance security are diverse and often tailored to individual needs. One such method offers a layer of obscurity that makes it harder for companies to collect specific details. By using innovative techniques, users can better control the flow of their information. This leads to a significant shift in how individuals engage with online platforms.
Amidst the rise of surveillance and profiling, protective measures have become essential. Users seek to reclaim their personal space within the digital landscape. By employing these advanced solutions, it is possible to create a safer online experience. Ultimately, having the ability to manage one's visibility is a crucial step toward personal autonomy in the virtual realm.
For anyone looking to take charge of their online footprint, understanding the mechanisms behind protective services is vital. Whether concerned about targeted advertising, unwanted solicitations, or simply wishing to enjoy the internet without intrusion, effective tools exist. These not only empower individuals but also serve as a barrier against invasive tracking practices. Thus, the journey toward greater personal privacy can begin with informed choices and strategic actions.
The Rise of Data Brokers

Understanding the intricacies of virtual private networks (VPNs) requires diving into their technological foundations. At its core, a VPN is a tool that creates a secure connection over a less secure network, such as the Internet. It helps protect users’ online activities and personal information from prying eyes. This technology is particularly relevant in today's digital landscape. There are many facets to consider when exploring this topic.
Firstly, let’s break down what makes a VPN function effectively:
- Encryption: It secures data by converting it into a code.
- Tunneling: It creates a private pathway for internet traffic.
- IP Masking: It hides the user's real IP address.
- Protocols: Various methods govern how data travels securely.
VPN technology operates on some fundamental principles that enhance user privacy and security. By utilizing various encryption techniques, a VPN safeguards sensitive information from potential cyber threats. This security measure is crucial for individuals seeking to navigate the online realm without leaving behind a trail of identifiable information. Additionally, through tunneling protocols, it allows users to send and receive data securely, masking their real IP address in the process. This anonymity factor contributes significantly to user privacy.
Understanding the specific types of protocols can illuminate how VPNs protect user information. Common protocols include OpenVPN, L2TP/IPsec, and IKEv2. Each has its advantages and potential drawbacks, making it essential for users to choose wisely. When selecting a provider, one should consider factors such as speed, encryption strength, and compatibility.
Moreover, VPNs can be instrumental for individuals and businesses alike. They can prevent unauthorized access to sensitive information during transmission. In an era where cyber threats are an everyday concern, this technology is not only relevant; it is essential. As society increasingly relies on the internet for various tasks, VPNs offer a crucial layer of protection against surveillance and data interception.
In conclusion, grasping the fundamentals of VPN technology empowers users to make informed decisions regarding their online safety. By understanding how virtual private networks function, individuals can better navigate the complexities of digital privacy in today's interconnected world.
Understanding VPN Technology
In today's world, where online privacy becomes increasingly important, a specific technology stands out. It provides an additional layer of security and anonymity. By masking one's identity and encrypting connections, this tool helps users navigate the internet with greater confidence. Many are unaware of how it functions and what makes it essential for maintaining privacy.
At its core, this technology creates a secure tunnel between a user’s device and the internet. It does this by routing connections through a remote server, which effectively hides the user’s real IP address. This process not only shields personal information but also allows access to content that might otherwise be restricted based on geographic locations.
- Encryption of online activities.
- Masking of IP addresses.
- Access to restricted content.
- Protection against eavesdropping.
Understanding the components of this technology can demystify its workings. First, encryption ensures that any data sent over the network is safe from prying eyes. This process transforms the information into unreadable code, making it nearly impossible for cybercriminals or even internet service providers to discern what is being transmitted. Second, by utilizing a remote server, users can effectively adopt a new virtual location, further enhancing their anonymity and enabling them to bypass censorship or content restrictions that may apply in their physical location.
It's also crucial to consider the protocols involved in this technology. Various protocols serve different purposes, offering varying levels of security and speed. For example:
- OpenVPN: Highly secure, widely used.
- IPSec: Ensures secure data transmission over IP networks.
- L2TP: Combines features of both IPSec and other protocols.
- PPTP: Older, but very fast; however, less secure.
With a better grasp of how this technology operates, users can make informed choices. It’s essential to select a reliable provider that prioritizes user privacy and employs strong encryption methods. By understanding the intricacies of how this tool functions in the online landscape, individuals can better safeguard their personal information and enhance their online experience significantly.
Privacy Threats from Data Sharing
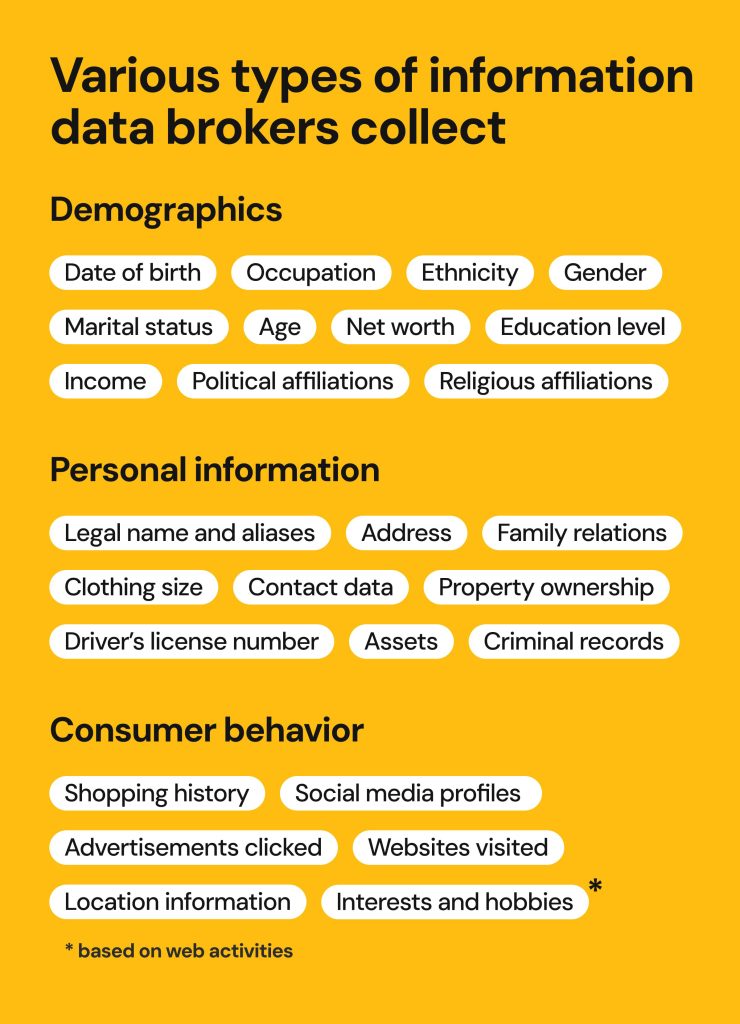
In today's interconnected world, sharing personal information has become routine. With every online transaction or social media interaction, fragments of our private lives are collected. This information can easily be aggregated, creating detailed profiles that many might find alarming. The implications for privacy are far-reaching. As our data circulates, the potential for misuse increases dramatically.
As organizations and entities utilize technology to harvest information, individuals often remain unaware of the extent of this collection. Many users unknowingly consent to terms that allow companies to track their activities extensively. Moreover, this accumulation of data can occur across multiple platforms, creating a comprehensive overview of someone's habits, preferences, and even vulnerabilities. This extensive tracking fosters an environment where personal privacy is continuously at risk.
In addition to ordinary web browsing, personal details can be gathered through various means. For instance, loyalty programs, mobile apps, and even simple website cookies are common channels. Each interaction adds another layer to the digital footprint, making it easier for outside parties to build a profile. Such practices not only violate personal privacy but also exploit the information for commercial gain.
Consider this: a seemingly innocent online survey or a free app may ultimately compromise your privacy. Companies often leverage this information to sell targeted advertisements, sometimes leading to unsolicited communications and spam. Furthermore, in worse-case scenarios, sensitive information may be exposed through breaches, leaving individuals vulnerable to identity theft.
To illustrate these threats, here is a table highlighting common methods used to collect information:
| Collection Method | Description |
|---|---|
| Cookies | Small data files stored on your device to track activity. |
| Surveys | Feedback forms that collect various personal data points. |
| Social Media | Platforms gather user info based on interactions and posts. |
| Mobile Apps | Applications often request access to contacts and location. |
| Loyalty Programs | Customers provide personal data for rewards and discounts. |
Ultimately, awareness of how personal information is collected is crucial. Recognizing these practices can empower individuals to take proactive measures. As people become more informed, they can better protect their privacy and respond effectively to potential threats.
Privacy Threats from Data Sharing
In today’s digital landscape, preserving one’s privacy has become increasingly challenging. Information flows freely across networks, often without individuals even realizing it. Each online action contributes to a vast pool of collected insights. These insights can be utilized in ways that infringe upon personal confidentiality. Understanding potential risks is essential for anyone wishing to safeguard their information.
Many entities thrive on collecting and disseminating personal profiles. This practice leads to significant privacy concerns. The more individuals engage with various platforms, the more vulnerable they become. Often, users unwittingly agree to broad terms that permit extensive information sharing. Consequently, unwarranted exposure becomes a serious threat.
- Unwanted advertising targeted based on personal habits.
- Potential for identity theft through exposed sensitive information.
- Unauthorized sharing with third parties without consent.
- Manipulation by companies using behavioral profiles.
- Increased risk of phishing attacks targeting individuals.
As platforms accumulate vast amounts of personal information, the implications for privacy grow more profound. Individuals often underestimate how many details are available to others, leading to a false sense of security. Constant monitoring and harvesting of personal data mean that even seemingly harmless activities might contribute to a larger narrative that could be exploited. Security breaches have become alarmingly common, leaving many feeling exposed and powerless.
Compounding these issues is the fact that many users remain ignorant of how their information is handled. Lack of transparency allows companies to operate with minimal accountability, resulting in situations where personal data can be misused. Moreover, regulations intended to protect privacy often lag behind technological advancements, further complicating efforts to maintain confidentiality. This environment underscores a critical need for individuals to take proactive steps towards safeguarding their own information.
Utilizing privacy tools can significantly diminish these risks. Taking action against unnecessary data collection equips individuals with greater control. Adopting practices that prioritize privacy can drastically alter the landscape of personal security. It’s essential to be aware of options available for enhancing protection, thus paving the way for a more secure online experience.
VPNs as a Privacy Tool
Protecting personal information has never been more critical. With constant threats to privacy, many individuals seek ways to safeguard their online presence. Several tools exist, each offering unique solutions. Among these, certain technologies stand out for their effectiveness. Understanding how to leverage these tools can significantly enhance personal security.
As people grow increasingly aware, concerns about online security escalate. Here are a few reasons why individuals should consider enhancing their privacy:
- Protects against intrusive monitoring.
- Encrypts connection, making it difficult for others to intercept.
- Masks IP address, providing anonymity while browsing.
- Bypasses geographic restrictions on internet content.
- Safeguards sensitive information when using public networks.
Encryption technology plays a vital part in maintaining confidentiality. When engaging in activities online, sensitive details can be exposed. Utilizing a VPN ensures that information travels securely between the user and the intended destination. This creates a safe tunnel, preventing unauthorized access by third parties. Moreover, it has become increasingly relevant in today's digital landscape, where cyber threats lurk at every corner.
However, the effectiveness of this protective measure can vary significantly depending on the choice of provider. Not all services offer the same level of security. Some may prioritize user privacy, while others might compromise it for profit. Conducting thorough research before selecting a service is crucial. Consider factors such as encryption methods, logging policies, and customer reviews.
In addition to selecting a trustworthy service, users should implement other privacy-enhancing practices. Regularly updating passwords, using two-factor authentication, and being cautious about sharing personal information online are essential habits. Together, these measures create a robust framework for personal security in an ever-evolving digital world.
Ultimately, employing an effective VPN can significantly enhance online experiences. By combining this tool with mindful behavior and continuous education about online threats, individuals can take substantial steps towards protecting their personal information. The pursuit of privacy is an ongoing journey that requires diligence, awareness, and the right set of tools.
Steps to Protect Your Data
In today's interconnected world, safeguarding personal information has become crucial. Many individuals are unaware of how easily their privacy can be compromised. Awareness and proactive measures can significantly enhance your security. It is important to adopt a multi-layered approach in this digital age. Simple actions can lead to meaningful changes.
Start by evaluating your online activities. Are you sharing more than necessary? Limit what you disclose on social media platforms. Check privacy settings regularly. Ensure that only trusted connections can view your information. Compromised accounts can lead to unauthorized access and exposure.
Utilizing strong, unique passwords is essential. Weak or repeated passwords are an open invitation for hackers. Consider using a password manager to store your credentials securely. This tool can help generate random passwords, enhancing your overall security posture. Additionally, enable two-factor authentication wherever possible; adding an extra layer can deter potential intruders.
Be cautious while browsing the internet. Many websites track your activities without consent. Using ad-blockers and privacy-focused browsers can minimize unwanted surveillance. Regularly clearing your browser cache is another good practice, as it helps delete tracking cookies that may store your information. It’s important to stay vigilant, as threats constantly evolve.
Utilizing alternative search engines can provide better privacy. Traditional search engines often collect extensive user data. Consider options that prioritize user anonymity and do not track search history. These tools can offer a Learn more on Medium secure online experience while ensuring that your inquiries remain private.
| Action | Description |
|---|---|
| Limit Social Sharing | Be mindful of what you share online. |
| Unique Passwords | Use diverse passwords across different accounts. |
| Browser Privacy | Utilize privacy-focused tools and regularly clear cache. |
| Alternative Search Engines | Choose search engines that prioritize user anonymity. |
Education is another vital aspect of protecting oneself. Keep informed about new threats and vulnerabilities. Threat landscapes shift quickly, and being aware can help you stay ahead of potential risks. Attending workshops or reading articles focused on cybersecurity can provide insights into best practices. Remember, your security is often only as strong as your knowledge and awareness.
Finally, consider reviewing your subscriptions and online memberships. Do you still need them? Unsubscribe from services that are no longer useful. Ensure that you only engage with platforms that respect and prioritize user privacy. Taking control of your online presence is a significant step towards ensuring your information remains protected.
Evaluating VPN Providers
Choosing a suitable service for secure online browsing can be challenging. Numerous options exist, and each provider offers unique features. Understanding specific aspects can significantly simplify the decision-making process. It's essential to consider several factors to ensure your choice meets privacy needs.
- Security Features: Look for robust encryption protocols.
- Privacy Policy: Assess the commitment to user data protection.
- Server Locations: A wide network improves access to global content.
- Speed and Performance: Check reviews about connection quality.
- Customer Support: Reliable assistance is crucial in emergencies.
An effective provider offers a blend of critical elements that enhance user experience, such as responsiveness and reliability. A transparent privacy policy is essential; it indicates how your information will be handled. Regular updates and continuous improvements reflect a commitment to user safety.
- Research: Investigate user reviews and expert opinions.
- Trial Period: Utilize free trials to test the service firsthand.
- Comparison: Evaluate multiple options side by side for better insight.
While exploring various providers, keep in mind that marketing claims can be misleading. Always prioritize your security and privacy over flashy advertisements. Additionally, a trustful service should not store logs of your online activity, ensuring anonymity during your browsing experience.
Making an informed choice requires careful consideration of the outlined criteria. Understanding what each provider offers leads to better decisions. The right choice can enhance your online security substantially, allowing you to surf the web with confidence.
- 이전글10 Unexpected Replacement Vauxhall Key Tips 24.09.21
- 다음글Why You Should Concentrate On Enhancing Rolls Royce Key For Sale 24.09.21
댓글목록
등록된 댓글이 없습니다.
